SMART CARD AND FINGERPRINT VEHICLE LICENSING

1 BACKGROUND
Driving without driving license is a major issue in many countries. Survey says that the accidents happened mostly by the unlicensed drivers, drunken drivers and less usage of seatbelts. Owing to unsafe conditions on roads, the rate of accidents in India has been high. In this current world where technology is growing up day by day and scientific researchers are presenting new era of discoveries. At present, the vehicle usage is basic necessity for everyone. Biometric systems are modern and techniques like fingerprint recognition, iris recognition and facial recognition are becoming popular. Of these, fingers print recognition and detection systems are easy to deploy, sophisticated and persons can be identified without their knowledge.
Biometric identification based security systems are considered to be the most secure especially due to their ability to identify people with minimal ambiguity. It uses a finger print detection and recognition system that identifies and verifies a person automatically by extracting unique features from an image. Fortunately, automated biometrics in general can provide a much more accurate and reliable user authentication method and fingerprint recognition is widely used. Identifying a person based on his or her physiological characteristics is the key factor of biometric recognition.

1.2 OBJECTIVES
is a mandatory part. This tedious and hectic procedure inspired us to think about the present RTO system and also motivated us
to implement this system which increases the robustness and efficiency An individual has to carry license and vehicle documents, if he fails to present those at the time of certain on road investigation by Government authority, He has to pay
the fine, here carrying documents of RTO
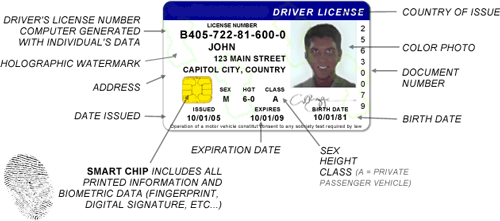
system and traffic issues. We would implement this system on android to give portability to system. The fingerprint recognition technique will help to identify whether the person is authorized to drive the vehicle or not.The proposed system consists of smart card (driving license) capable for storing the fingerprint of a particular person. While issuing the license, the specific person’s fingerprint is to be stored in the card. First, the person should insert the smart card (driving license) and provide the finger print. If the fingerprint matches with the fingerprint stored in the smart card then it goes for alcohol detection and seatbelt checking. A person is checked by alcohol detector whether that person is drunk or not. Seat belt detector verifies and prompts the person to wear the seatbelt.
PROBLEM STATEMENT
The main objective is to develop technology that include android application and web application to provide digitalization to both, an individual and RTO system, by reducing the documentation part.
Currently the traffic police use a manual process for identifying and verifying authority of a person. However, people have to face many problems with the current procedure used by the traffic police. According to public point of view there is no facility provided by the RTO which will make the person document free. The main problem with the existing system is that either people have to carry their documents or smart card, but there is possibility that the information might get lost.
Today android devices play an important role in our day to day life since most of the tasks can be done on android device. Since the people have to carry documents regarding the information of the vehicle, the police as well as people have to face many problems. Thus the traffic police app not only reduces the task of the police but also makes the person document free.
2.1 EXISTING SYSTEM
Unlicensed driving is a matter of concern for several reasons. It is possible that drivers who have not undergone appropriate training and testing may be deficient in some aspect of knowledge & skills required to drive safely & efficiently. In the Existing system every user should carry the driving license along with them.To avoid this we proposed a new system.
Disadvantages of Existing System:
- Unlicensed persons can drive the vehicle
- Causes many Accidents
- Users should keep the license always with them
The design and the development of a prototype of an interfacing between PIC and smart card that is important in car security application. Smart card was used, as one of the cheaper way to prevent the car from robbery or theft. Each smart card supplied with machine ID that are set in the microcontroller’s memory for authentication purposes. Here, the smart card function is similar to an external EEPROM chip; therefore for simplicity external EEPROM chip was used to replace the smart card. The software kits developed to help users to set an ID. Visual Basic 6.0 was used as interfacing with microcontroller chip 16F877A. Each registered user supplied with different smart cards of difference ID but with the same machine ID. This could be used in the system to ensure only the authenticated person can
use the particular cars. Smart card is commonly used in security system that has the ability to secure information. In the past few years, security system has been used in many areas and applied in many fields such as corporate organizations, government, bank, and etc. as security access system. Its popularity is increasing due to its low in price and safety. Smart card has now been used extensively in the vehicle security system to prevent unauthorized access and to reduce vehicle robbery or theft especially on a car.
Most of the cars nowadays are equipped with alarm security systems which notify users through buzzing the alarm. However, as technology grows, this security system can be easily defeated. Cars are stolen not because thieves’ possess fine engineering skills but due to the weaknesses of the systems. This currently does not indicate as professional engineer but it is based on the familiarity and brute force methods. The work presented demonstrates the simulation and development of the smart card securitysystem for cars. Despite as an initial work, it shows that the communications of data transmission has workedsuccessfully. However, some important thing can be highlighted, is the mechanism when the card itself is stolen or missing. Further improvement of the system will consider the intelligent features by applying artificial intelligence techniques and adding some sensor using RFID technology to detect the smart card without waving at the reader.
This paper proposes a methodology for tracking systems based on the global positioning system and radio communications to determine the current location of moving objects, such as a vehicle, and sends this information to a remote monitor center. The designed system consists of two units, which are the vehicle unit and the monitor unit. When theft of vehicle is detected, the monitor unit sends a packet that automatically turns off the vehicle engine, which provides real time control. The data at monitor unit are stored in a file and can be retrieved as requested for route browsing on a Google map. A graphical user interface application is developed using Visual Basic with embedded Google map to retrieve and display vehicle current position. The proposed embedded system can be considered a
successful one as it is small size, low power consumption, and implemented on a single chip microcontroller with low cost. Due to the rapid development in
telecommunications and information technology there is a need to build a modern
information system which will be useful for many applications such as auto tracking, stalking, anti-theft, and traffic control, where all these systems benefit from a global positioning system (GPS). Whereas the use of radio frequency (RF)
communication transceiver and GPS system inside the vehicle leads to provide a lot of information that can be collected, wireless transferred, and lead to the integration of all the above-mentioned applications in one complex system.
Nowadays, it is noted that a large increase in the number of vehicles in the roads, causing a high rate of vehicle theft and increase number of accidents. Vehicle tracking introduces open communication channels. So that sophisticated strategies for secure communication are necessary. Secure communication is mainly based on encryption and authentication in order to provide confidentiality and authenticity of exchanged data. There is a variety of literature available about secure communication. The developed system used to display the current positionof the tracked vehicle in the GUI and Google map. The objectives of the system are satisfied successfully. The developed system should be placed inside the vehicle in a suitable place so that it would not to be detected by the thief or not authorized person. The system sends the current location of the vehicle identified by the GPS to the monitor unit using RF channel. When the theft is identified, the vehicle engine can be turned off by sending a signal from the monitor unit to thevehicle unit. The simulation of the whole system had been done using proteus software.
The system owns many advantages over others such as represent real time tracking, work in places that lack coverage of GSM networks, for example in rural areas and highways, low costs, small size and portable, effective, easy to use with Pc. For future needs it is very easy to add new facilities to the system. We can reduce the error resulting from the GPS reading by using high accuracy receiver or the use of more than one GPS receiver. We can add a facility to display the route of more than one vehicle at the same time on the map, for example for companies that have many vehicles. In addition to at, the system in the future can support biometric security approach for authentication, such as using finger print, iris, voice or hybrid to distinguish between the owner and the thief.
Recently, several companies have introduced passive entry systems for automotive applications. These systems are intended to increase user comfort by eliminating the requirement that the user has to reach for the customer identification device (CID), a credit card like tool, to gain access to the vehicle compartment. While this extra level of comfort is a desirable feature, especially in luxury vehicles, it introduces several key attacks against the system. This paper describes several techniques of potential attacks against the passive entry system and proposes solutions to protect the vehicle from such attacks. The user was required to enter a unique digital code through the keypad to unlock or lock the vehicle. Since then, the use of keyless entry systems has grown rapidly, and the demand for a greater level of ease of use has increased. These demands led the automotive industry to introduce the remote keyless entry system (RKE).
Modern vehicles are increasingly being interconnected with computer systems, which collect information both from vehicular sources and Internet services. Unfortunately, this creates a nonnegligible attack surface, which extends when vehicles are partly operated via smartphones. In this letter, a hierarchically distributed control system architecture which integrates a smartphone with classical embedded systems is presented, and an ad-hoc, end-to-end security layer is designed to demonstrate how a smartphone can interact securely with a modern vehicle without requiring modifications to the existing in-vehicle network. Our proposed solution allows a smartphone to establish a secure session layer over an insecure radio connection, which provides additional security guarantees regardless of the security mechanisms already implemented in the physical layer (if any). As a result, the entire application layer is transparently secured. Analyzed and discussed the security issues related to modern, smartphone-based automotive embedded architectures. To cope with such issues, we designed, implemented and evaluated a security layer that protects from an attacker that has full control over the Bluetooth wireless link between themobile device and the vehicle.
2.3 PROPOSED SYSTEM
The proposed system contains five modules:Fingerprint reader, Card Reader, Fingerprint matching, Seatbelt detection, Ignition control. Fingerprint reader is the first step of the system in that scan the users Fingerprint.Card Reader in that user swap his license on card reader and card reader read the fingerprint store on card. Next step is the matching in this system will check the user fingerprint and store fingerprint are matched or not.After matching the fingerprints it will check for seat belt whether user wear a seat belt or not if yes it will start ignition control otherwise it will give alarm to the user to wear seat belt.

2 Fingerprint Matching Algorithm
Fingerprint identification is one of the most popular and reliable personal biometric identification methods. This paper describes an on-line fingerprint identification system consisting of image acquisition, edge detection, thinning, feature extractor and classifier. The preprocessing part includes steps to acquire binarized and skeletonized ridges, which are needed for feature point extraction. Feature points (minutia) such as endpoints, bifurcations, and core point are then extracted, followed by false minutia elimination. Human fingerprints are rich in details called minutiae, which can be used as identification marks for fingerprint verification. The algorithm that was implemented for finger print matching in this research work is discussed below. Anil Jain proposed a hybrid matching algorithm for matching. Our algorithm is described in detail below.
STEP1. Histogram Equalization:
Histogram equalization is to expand thepixel value distribution of an image so as to increase the perceptional information. The original histogram of a fingerprint image has the bimodal type the histogram after the histogram equalization occupies all the range from 0 to 255 and the visualization effect is enhanced.
STEP2. Fourier Transform:
Because the image in the Fourier domain is decomposed into its sinusoidal components, it is easy to examine or process certain frequencies of the image, thus influencing the geometric structure in the spatial domain.
STEP3. Binarization:
A locally adaptive binarization method is performed to binarize the fingerprint image. Such a named method comes from the mechanism of transforming a pixel value to 1 if the value is larger than the mean intensity value of the current block (16×16) to which the pixel belong.
STEP4. Direction:
Field orientation and filtered field orientation map computation, which consists of the calculation of the dominant direction of ridges and valleys in each local region.
STEP5. Region of Interest (ROI):
Two Morphological operations called ‘OPEN’ and ‘CLOSE’ are adopted. The ‘OPEN’ operation can expand images and remove peaks introduced by background noise. The ‘CLOSE’ operation can shrink images and eliminate
small cavities.
STEP6. Thinning:
The built-in Morphological thinning function in MATLAB is used for ridge thinning. The thinned ridge map is then filtered by other three Morphological operations to remove some H breaks, isolated points and spikes.
STEP7. Matching:
A bounding box is placed around each template minutia. If the minutia to be matched is within the rectangle box and the direction discrepancy between them is very small, then the two minutia pair is regarded as a matched minutia pair. Each minutia in the template image either has no matched minutia or has only one
corresponding minutia. The number of matched minutia pair is calculated as percentage of matching.
SOURCE CODE AND MORE INFORMATION
CONTACT : amalanto18@gmail.com
THANKS…